Open a tunnel. You can open a secure tunnel using the AWS Management Console, the AWS IoT API Reference, or the AWS CLI. You can optionally configure a destination name but it’s not required for this tutorial. If you configure the destination, secure tunneling will automatically deliver the access token to the remote device using MQTT.. RemoteIoT uses the AWS IoT cloud platform, which is a secure way to connect IoT devices from anywhere you want. It provides a safe mechanism to encrypt and encapsulate private network traffic and move it with the help of an intermediate network. The remote IoT platform enables developers to connect IoT devices in a web browser as an SSH client.
GitHub awssamples/awsiotsecuretunnelingwebssh A pure webbased SSH client that acts as a

Top 10 IoT Devices Critical To The New Digital Revolution
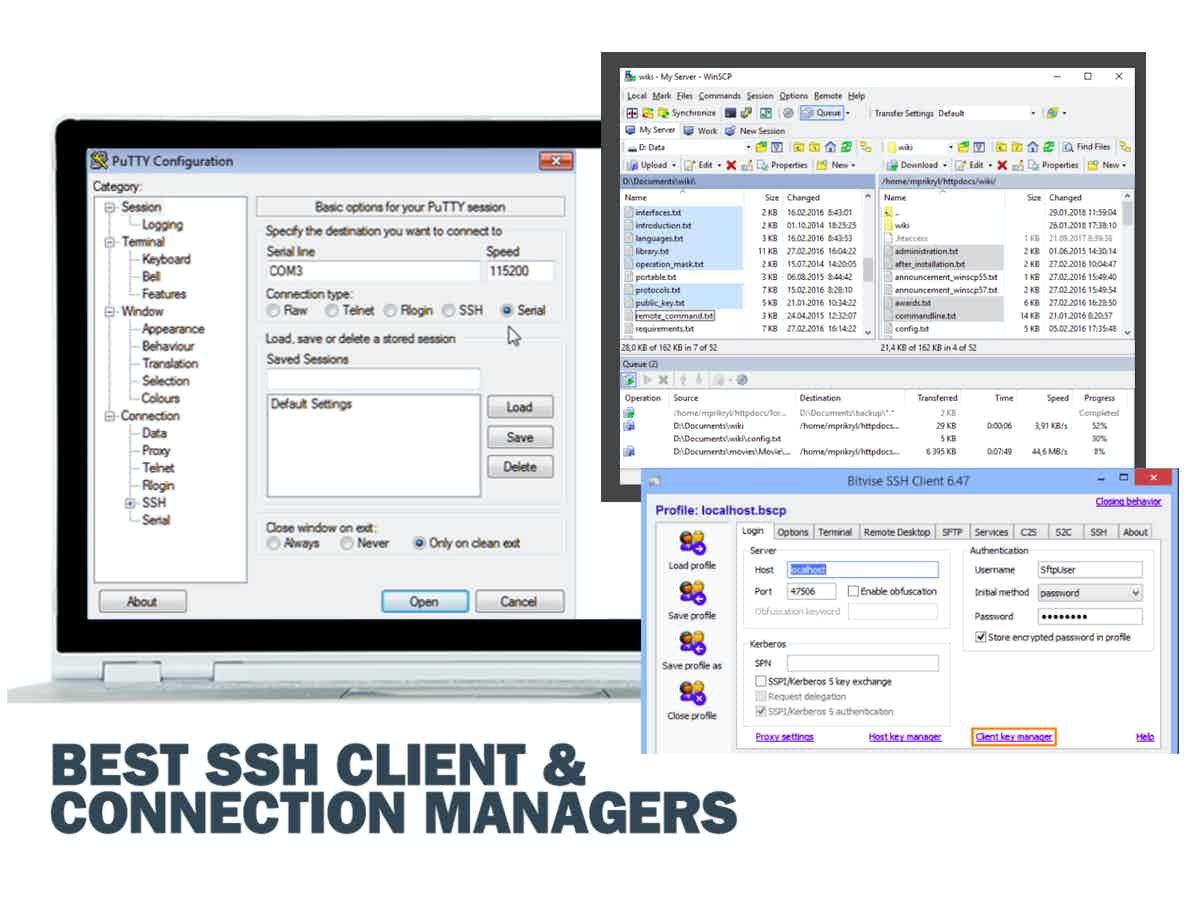
10 best ssh clients for windows adalasopa
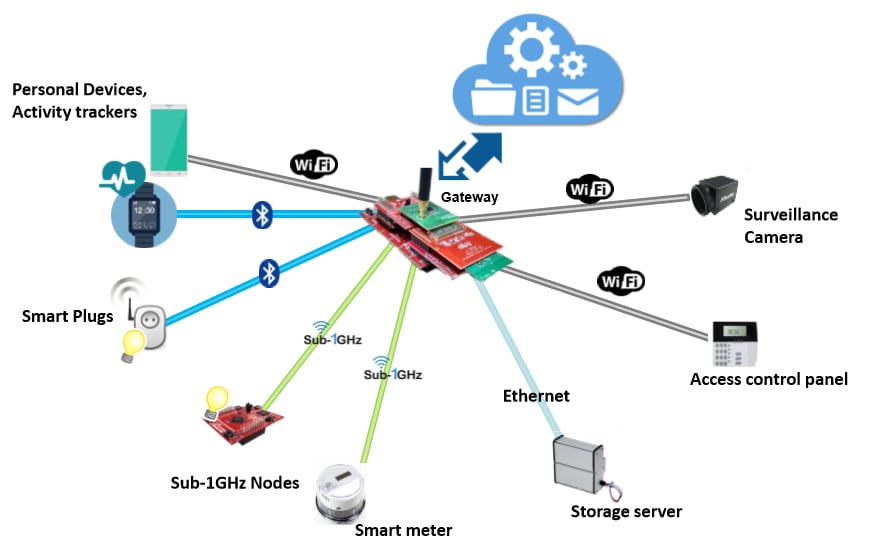
How Gateways Can Secure IoT Architectures Bench Talk

Top 20 IoT Devices List You Must Know MindMajix

10 Most Popular IoT Devices That Really Work Well In 2020 FROMDEV

Access IoT Devices from Anywhere Pinggy

How IoT Technology Improves Your Business Adapt IT
How IoT Works 4 Main Components of IoT System DataFlair
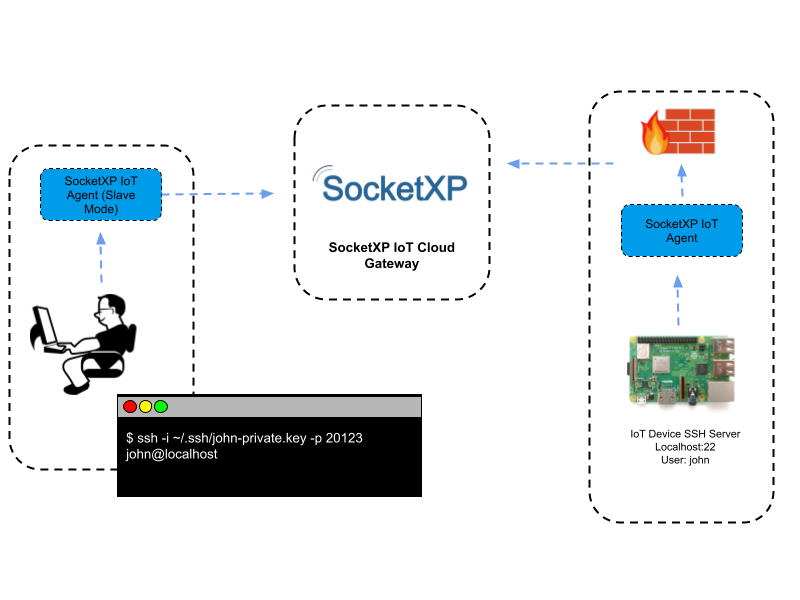
Remote SSH into IoT devices or Raspberry Pi behind NAT router or firewall from outside network

Secure Remote Access to Your IoT Devices Tinkerman

Secure access to Devices with SSH Explore networkhope.in

Everything You Need to Know About IoT Checkbox Technology
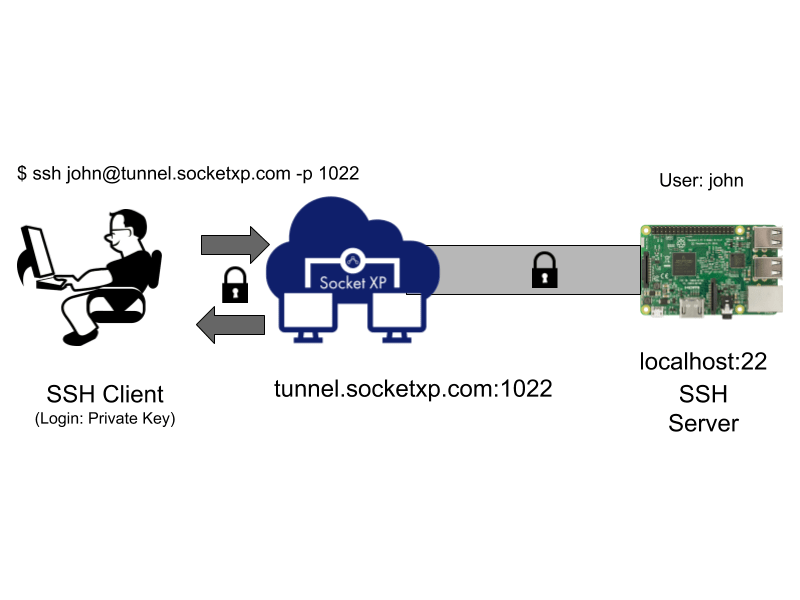
Secure remote SSH access to your IoT devices & Raspberry Pi fleet using SocketXP. DEV Community
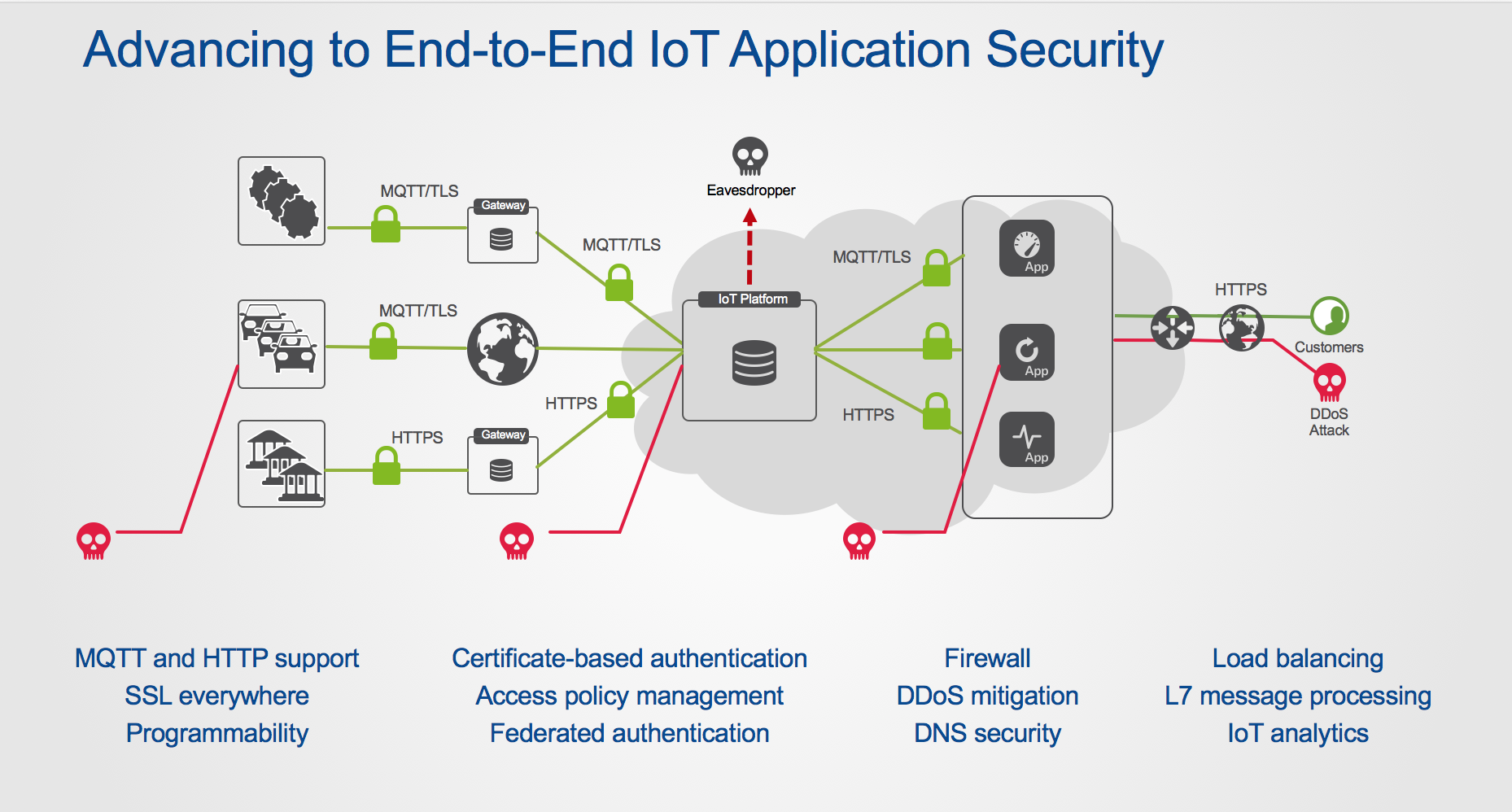
IoT Message Protocols The Next Security Challenge for Service Providers?
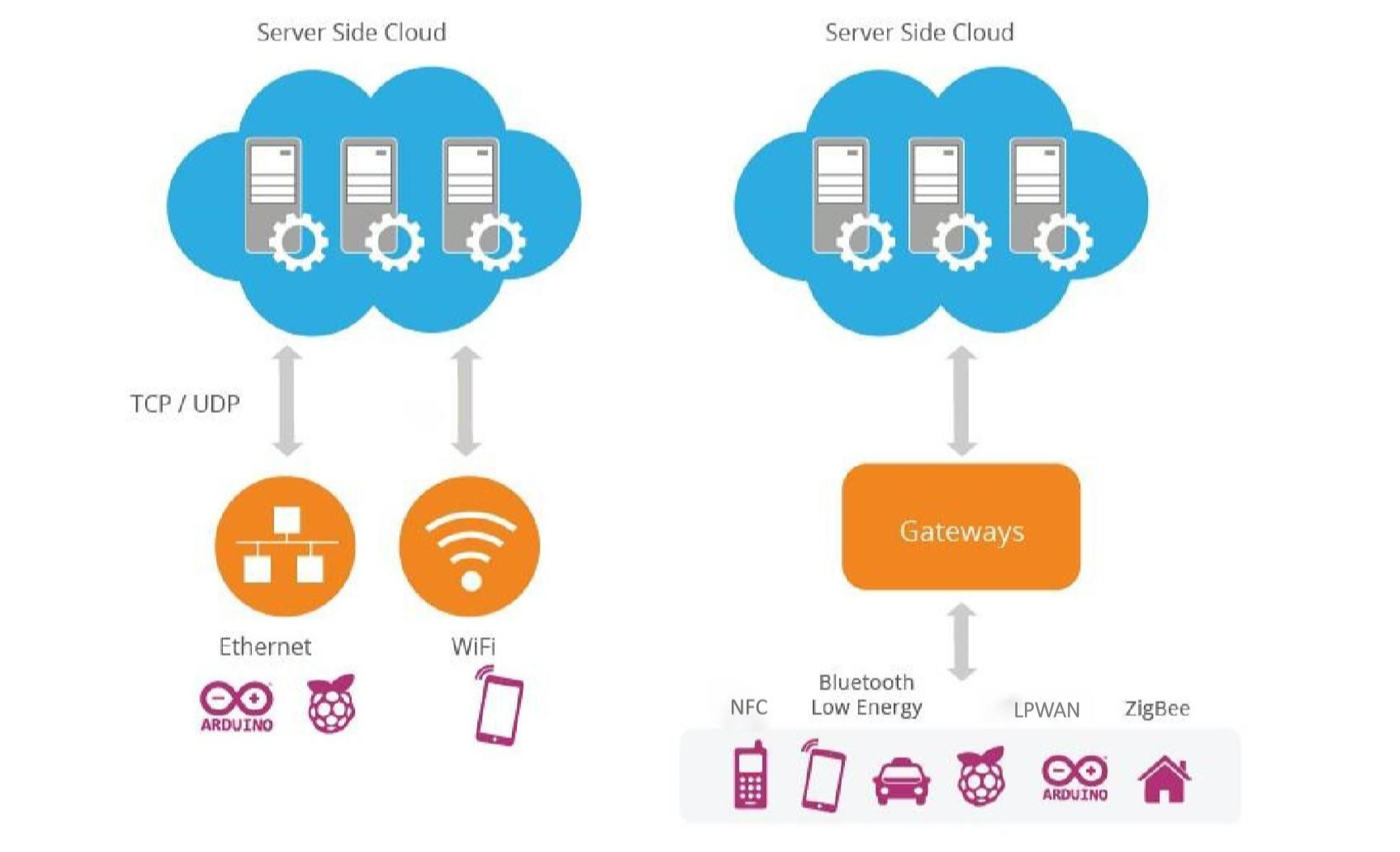
of Things (IoT) Architecture Key Layers and Components AltexSoft
Top IoT devices 2019 You Should Know!

How to Create SSH Port Forwarding
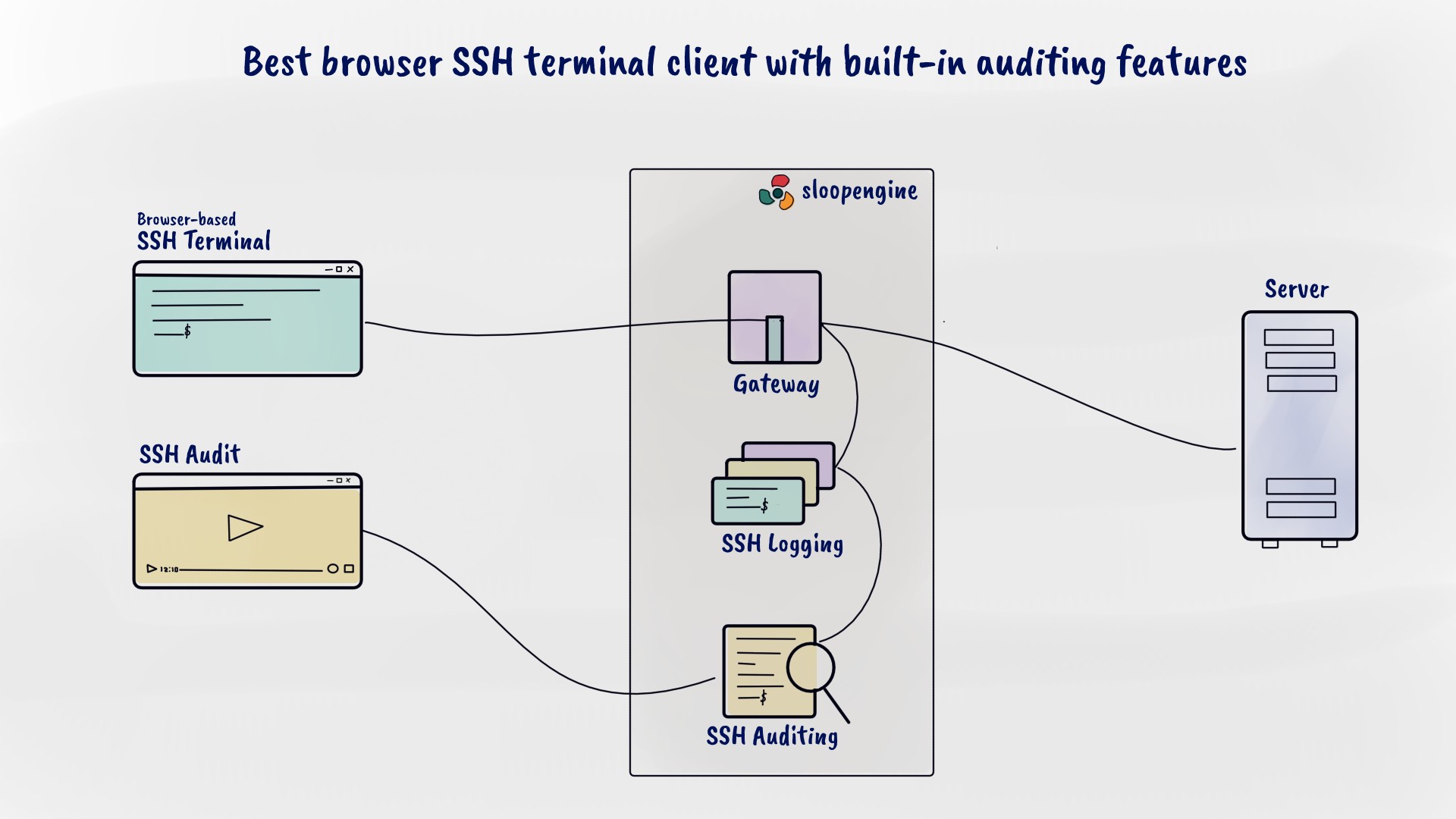
Best browser SSH terminal client with builtin auditing features SloopEngine Blog

Azure IoT Hub An Excellent Way To Manage Your IoT Devices Through The Cloud
To ensure secure remote access for IoT devices, the most used protocols are Secure Shell (SSH), Virtual Private Networks (VPN), and Remote Desktop Protocol (RDP). These technologies offer a safe way to connect remotely and enable management of IoT systems. What are some best practices for managing IoT remote access?. JFrog Connect is a modern Linux-first IoT platform designed to efficiently update, control and monitor edge and IoT devices at scale. Why and how you can remotely access IoT devices – Yocto based Linux, Raspberry Pi, Jetson Nano, etc. This post explains the idea behind the need and the best solution to control IoT and edge Linux devices.


